Product Overview
Product Overview
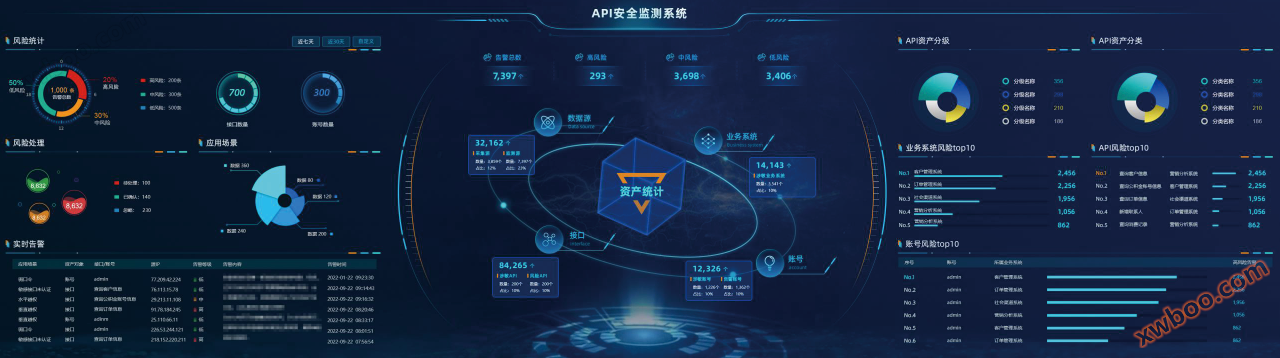
The API security monitoring system automatically discovers API asset data existing in the target system through network traffic or access logs, and incorporates it into the system for internal management. By monitoring the access of target API assets and addressing security risks, data leakage, abuse, and other issues that data interfaces may face, the effectiveness of API authentication, excessive exposure of sensitive data, API access behavior, and other security risk scenarios can be monitored. Combined with relevant models, suspected security issues in the access source and target API assets can be analyzed, and the ability to gather evidence and trace the discovered security risks can be achieved. The system adopts big data analysis technology, has powerful analysis engine capabilities, and is equipped with rich API security scenario monitoring models, which can optimize security event models according to the business of the enterprise.
 Features
Features
 API Asset Management:Use traffic probes to identify and discover sensitive data, accounts, interfaces, business systems, and other data assets in API interface traffic. According to the built-in classification and grading rules, classify and grade sensitive data, establish a sensitive data ledger, and provide support for data classification and protection.
API Asset Management:Use traffic probes to identify and discover sensitive data, accounts, interfaces, business systems, and other data assets in API interface traffic. According to the built-in classification and grading rules, classify and grade sensitive data, establish a sensitive data ledger, and provide support for data classification and protection.
 Security traceability analysis:Save the full amount of API raw traffic logs and actively associate API risk event alerts with alert logs. Directly obtain the source information of event alarms from the alarm traffic log, present the complete attack process of the event, help users conduct in-depth analysis and judgment of API security risk events, and quickly and accurately locate the cause of risk events.
Security traceability analysis:Save the full amount of API raw traffic logs and actively associate API risk event alerts with alert logs. Directly obtain the source information of event alarms from the alarm traffic log, present the complete attack process of the event, help users conduct in-depth analysis and judgment of API security risk events, and quickly and accurately locate the cause of risk events.
 Visual Operations:Perform secondary analysis, application, and display of asset data, strategy data, risk event data, and profile data generated during system operation to provide overall API security situation information for enterprises.
Visual Operations:Perform secondary analysis, application, and display of asset data, strategy data, risk event data, and profile data generated during system operation to provide overall API security situation information for enterprises.
 API risk monitoring:Based on the risk monitoring strategy of system configuration, analyze and discover the risks of authentication effectiveness, sensitive data exposure, asset information exposure, interface access behavior, and filing, and issue timely alerts.
API risk monitoring:Based on the risk monitoring strategy of system configuration, analyze and discover the risks of authentication effectiveness, sensitive data exposure, asset information exposure, interface access behavior, and filing, and issue timely alerts.
 Flexible feature expansion:Based on the data classification and grading engine, the processed data is automatically classified and graded by analyzing data features and combining them with data classification and grading strategies. Support effective enterprises to customize classification and grading standards and strategies based on industry requirements and business status.
Flexible feature expansion:Based on the data classification and grading engine, the processed data is automatically classified and graded by analyzing data features and combining them with data classification and grading strategies. Support effective enterprises to customize classification and grading standards and strategies based on industry requirements and business status.
 Multidimensional analysis of reports:Support multi-dimensional report analysis and provide the ability to export custom reports.
Multidimensional analysis of reports:Support multi-dimensional report analysis and provide the ability to export custom reports.
 Application scenarios
Application scenarios